Codes and Cryptography
Welcome to Chapter 2! This is a tutorial on the Common Codes and Ciphers! Ready? Let us begin!
I'll start with the simple ciphers first, then work my way up. Common words used here- ciphertext refers to the encoded message, while plaintext is the decrypted. A position in the alphabet refers to its place - for example, J is the 10th letter in the alphabet. Lastly, a 'key' is something used to encode - or decode - ciphertext using a formula.
The easiest is known as A1Z26. In this cipher, the letters are converted into their corresponding numbers based on their position in the alphabet. As such, A would become 1 and Z 26, hence the name. Thus, the ciphertext 8-5-12-12-15 would be 'hello' in plaintext. Generally, there will be few hints for this puzzle, due to its relatively unique way of encryption - it only contains numbers, stopping at 26.
Second is Atbash. Imagine the alphabet laid out in a straight line , such as ABCDEFGHIJKLMNOPQRSTUVWXYZ. Then, imagine that this line was folded into half, such that A would 'touch' Z, B to Y and so on. That is how Atbash works - the letters are changed to their respective 'mirror'. Hence, hello would be 'svool'. It originates from the Hebraic language in ancient history. In fact, its name is derived from the first, last, second and second-last letters of it respectively - Aleph, Taw, Beth and Shin giving 'atbesh', or Atbash. In fact, it was even used in the Bible, with 'Sheshach' in Hebraic being decoded to 'Babylon'. Potential clues could be something related to Hebrew, or perhaps mirroring.
Next is the Caesar cipher. It requires a number to be used as a key. From there, the plaintext letter is shifted down the alphabet, the shift being the key's number. For example, if the key was 3, A would be shifted to D, shifting three positions in the alphabet. It was invented by Gaius Julius Caesar and named as such. Generally, clues will either mention things to do with him (Rome, salad) or a number. As such, a possible puzzle would be 'zkyz vaffrk', the clue being 'June'. It would decode to 'test puzzle' when decoded using a shift of 6, which would be what June refers to.
After that is the Vigenere cipher. It is similar to Caesar, in a sense, yet is far more complicated. For one, the key is not a number, but rather a word or phrase. The first letter of the ciphertext is shifted by the first letter of the key's position, the second letter is shifted to the second, and so on. Note that the letter's original position would be considered a shift of 1 - hence, using 'A' as the key would not change anything. When either the key or the alphabet runs out of letters, it loops around. Thus, 'hello everyone' encrypted with the key 'key' would have H shifted by 11 positions - that's the position of K, after all -to R, E would be shifted 5 positions downwards to I, and L would be shifted 25 positions down to Z, before looping around back to A and eventually to J. The second L would shift 11 characters downwards as 'key' loops around, and repeats. Due to the near-infinite possible keys, clues will probably be specific to the actual key given.
The modern form of Vigenere was invented in the 1500s by Giovan Battista Bellaso - Blaise de Vigenere, to whom the cipher was attributed to, did not actually create it but rather made a variant known as Autokey, or Autoclave - the difference is that the key doesn't loop, but instead uses the plaintext as an extension to the key. Autokey was invented more than thirty years after Vigenere. Interestingly enough, Bellaso actually does have a cipher named after him, though that is too complicated to be covered here.
Next is Morse code.

Source: https://en.wikipedia.org/wiki/Morse_code
As can be seen, each letter of the alphabet becomes dots and dashes. Simple alterations could be using 1s and 0s instead of dots and dashes, or two different colours instead. It was created in order to communicate via incredibly early telegraphs. Common clues would be to do with the nature of the code, only having two symbols.
Another example of this form of cipher - where each letter is assigned to a certain symbol - is the Semaphore cipher.
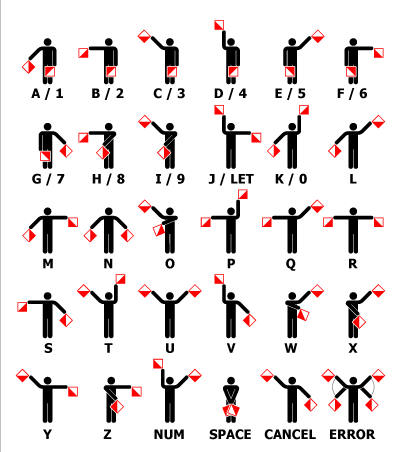
Source: https://www.boxentriq.com/code-breaking/semaphore-flags
Technically, it's not an actual cipher, since it was designed to communicate between two ships, or a ship and land. Still, it can be used as a form of enciphering a message, especially when the flags are disguised or altered (for instance, using toothpicks or simple lines instead of flags). Clues might be to do with flags or ships, but similarly to Morse code, this cipher is generally rather easy to identify by itself.
The six ciphers mentioned above are all substitution ciphers - in other words, the letters are converted into something else entirely, whether that be different letters, numbers or other symbols. Another type of cipher is known as a transposition cipher, in which the letters are not changed, simply rearranged.
One of the simplest forms of this is known simply as the columnar
transposition cipher. It requires a key consisting of letters. The text is
broken up into columns, the number of which are equal to the number of
lettters in the key. Thus, assuming a key 'key' is used to hide the phrase
'message', it would be broken up into:
'mes
sag
e'.
Sometimes, the letter x can be used to fill in an incomplete group, making
the last row 'exx'. I'll be using that for the example. The columns are
then rearranged according to the alphabetical order of the key. I'm quite
sure that a word with repeated letters, for example 'tart' would be
re-written as 'artt', with the first t being before the second. Since
'key' would therefore be rearranged to 'eky', the first and second rows
would be swapped, making it
'ems
asg
xex'
This will then be read out from top to bottom, left to right, making it
'eaxmsesgx', which would be the ciphertext. Common clues would probably be
to do with columns, though similarly to vigenere the clues will probably
refer to the key itself.
Well done! You finished Chapter 2! Click here to head to Chapter 3!